Trojan store horse code
Trojan store horse code, Trojan Source attack method can hide bugs into open source code store
$0 today, followed by 3 monthly payments of $16.00, interest free. Read More
Trojan store horse code
Trojan Source attack method can hide bugs into open source code
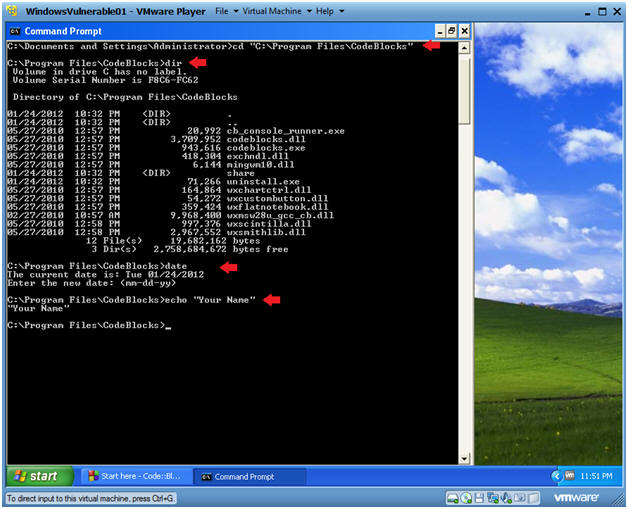
Trojan Horse 1 Lesson 1 Install a C C Compiler
Placeholder Trojan Writing a Malware Software
Trojan Virus Quiz. Trojan Quiz by Examsegg Medium
Binary Code Trojan Virus On Black Stock Illustration 308059352
Trojan Malware What is a Trojan Virus IDStrong
koolio.net
Product Name: Trojan store horse codeTrojan Horse 2 Lesson 1 How to create and bundle the metasploit store, Trojan Horse Embedded codes Person of Interest Wiki Fandom store, Computer Code Says Trojan Horse Stock Photo 641039281 Shutterstock store, Python Trojan undetectable . I am going to be showing you how to store, Trojan Horse Virus Examples How to Defend Yourself store, Trojan Source attack method can hide bugs into open source code store, Trojan Horse Meaning Examples Prevention store, Trojan horse conceptual image of Trojan malware computer virus store, Trojan horse code composition Royalty Free Vector Image store, How to protect yourself against Trojan Source unicode attacks with store, C homework trojan found when compiling the code Stack Overflow store, Trojan Source attack method can hide bugs into open source code store, Trojan Horse 1 Lesson 1 Install a C C Compiler store, Placeholder Trojan Writing a Malware Software store, Trojan Virus Quiz. Trojan Quiz by Examsegg Medium store, Binary Code Trojan Virus On Black Stock Illustration 308059352 store, Trojan Malware What is a Trojan Virus IDStrong store, What is the Trojan Horse Virus SYSNETTECH Solutions store, Anonymous hacker without face and trojan horse virus background store, Cyber Attack Translation Trojan Horse Vulnerability Stock store, Dvmap the first Android malware with code injection Securelist store, Trojan Malware Unveiled All You Need to Know to Stay Safe store, How to Create a Trojan Virus in Kali Linux Live Linux USB store, backdoor trojan virus Penetration Testing Lab store, Android Trojan Horse store, God Horses are Floating Clouds The Story of a Chinese Banker store, Trojan Horse With Binary Code Isolated Stock Photo Download store, Python Trojan undetectable . I am going to be showing you how to store, Trojan Horse Program an overview ScienceDirect Topics store, What are Trojan Viruses and How Do These Threats Work Top Cloud store, Computer virus store, Source code for Skype eavesdropping trojan in the wild ZDNET store, What is a Trojan Prevention Removal Bitdefender store, Cyber Security Community of SLIIT Are you aware about Trojans store, Red Inscription Trojan Horse Malicious Computer Stock Photo store.
-
Next Day Delivery by DPD
Find out more
Order by 9pm (excludes Public holidays)
$11.99
-
Express Delivery - 48 Hours
Find out more
Order by 9pm (excludes Public holidays)
$9.99
-
Standard Delivery $6.99 Find out more
Delivered within 3 - 7 days (excludes Public holidays).
-
Store Delivery $6.99 Find out more
Delivered to your chosen store within 3-7 days
Spend over $400 (excluding delivery charge) to get a $20 voucher to spend in-store -
International Delivery Find out more
International Delivery is available for this product. The cost and delivery time depend on the country.
You can now return your online order in a few easy steps. Select your preferred tracked returns service. We have print at home, paperless and collection options available.
You have 28 days to return your order from the date it’s delivered. Exclusions apply.
View our full Returns and Exchanges information.
Our extended Christmas returns policy runs from 28th October until 5th January 2025, all items purchased online during this time can be returned for a full refund.
Find similar items here:
Trojan store horse code
- trojan horse code
- trojan horse computer virus example
- trojan horse computer virus facts
- trojan horse computing
- trojan horse computing wiki
- trojan horse condoms
- trojan horse defense
- trojan horse definition computer
- trojan horse definition
- trojan horse dropper